Attribute Based Access Control
Enforce fine-grained access to application and resources based on universal policies, user attributes, and context with Warrant.
Policy Based Access for Modern Teams
Add fine grained, policy-based access control to your applications in minutes. Enforce, manage, and audit your access policies in real-time.
1#2# Only users coming from a specific range of IPs can access prod.3#4warrant assign \5 env:prod editor user:ops-eng \6 [ip startsWith '214.158']7
8#9# Assert user:ops-eng cannot access prod from non-allowed IP.10#11warrant check \12 env:prod editor user:ops-eng \13 '{"ip":"134.146.24.10"}' --assert false14
15#16# Assert user:ops-eng can access prod from non-allowed IP.17#18warrant check \19 env:prod editor user:ops-eng \20 '{"ip":"214.158.18.10"}' --assert true21
22
23
24
25
26
27
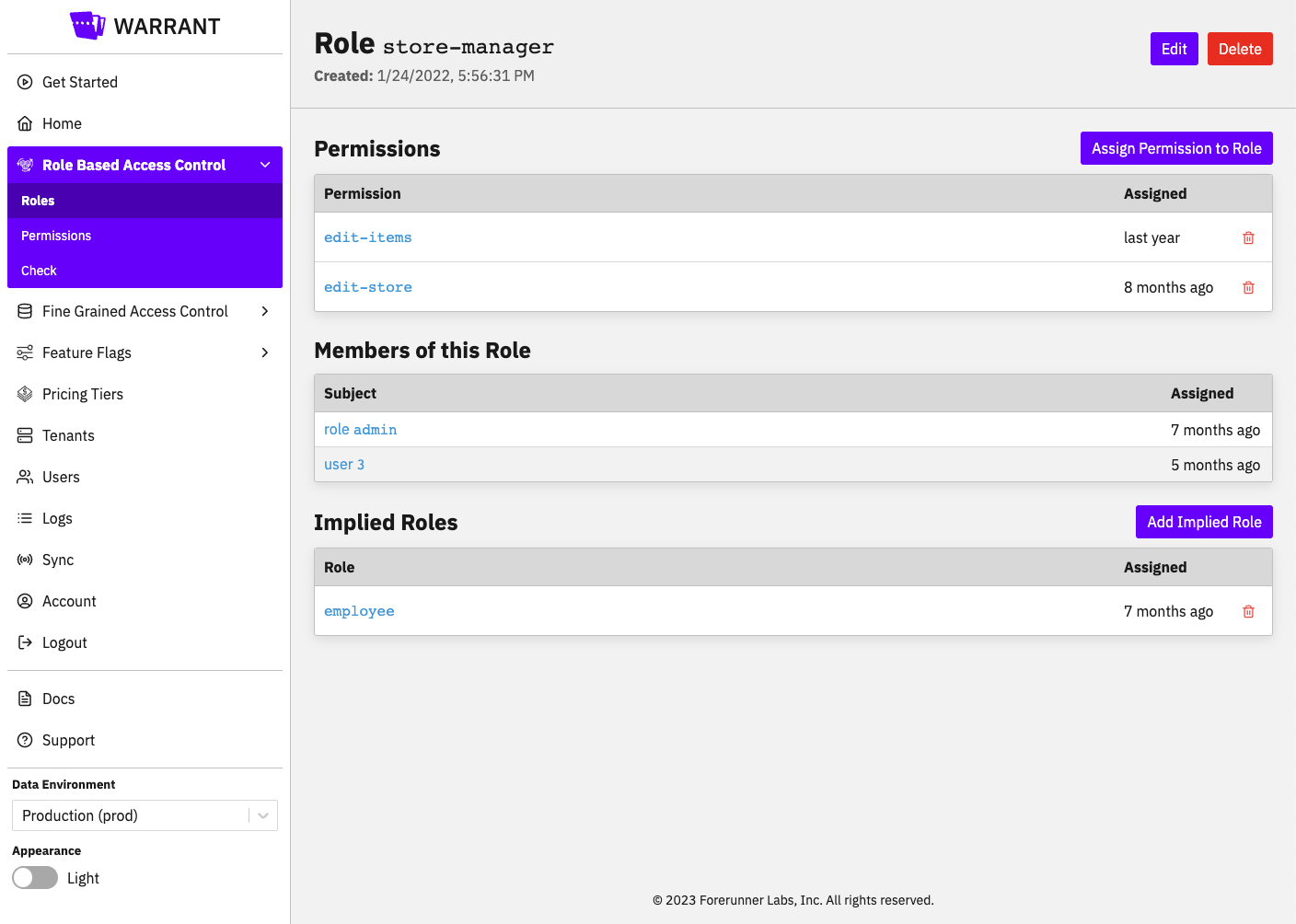
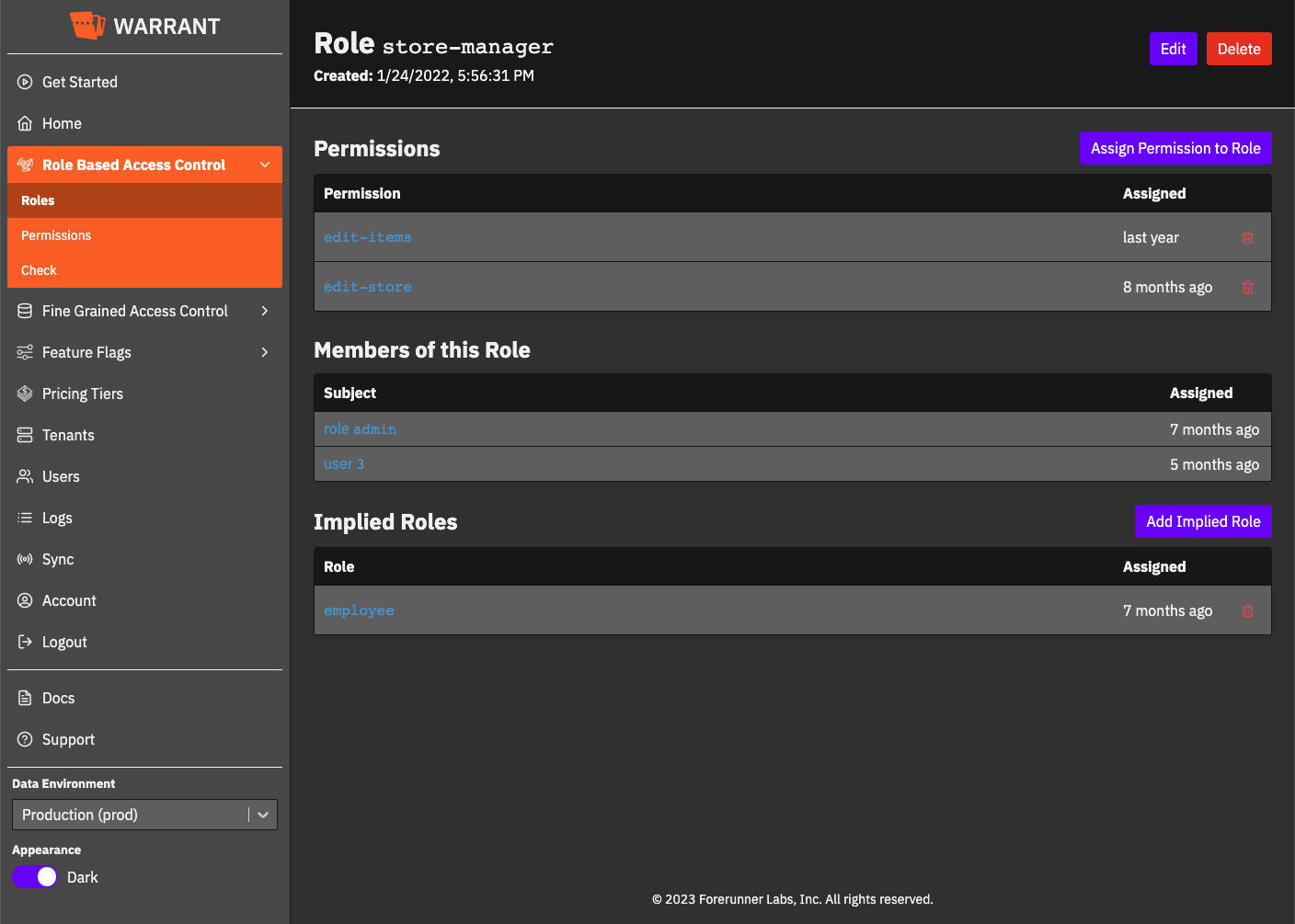
Management Dashboard
Manage policies and entitlements without code changes through an intuitive management dashboard built for both technical and non-technical users.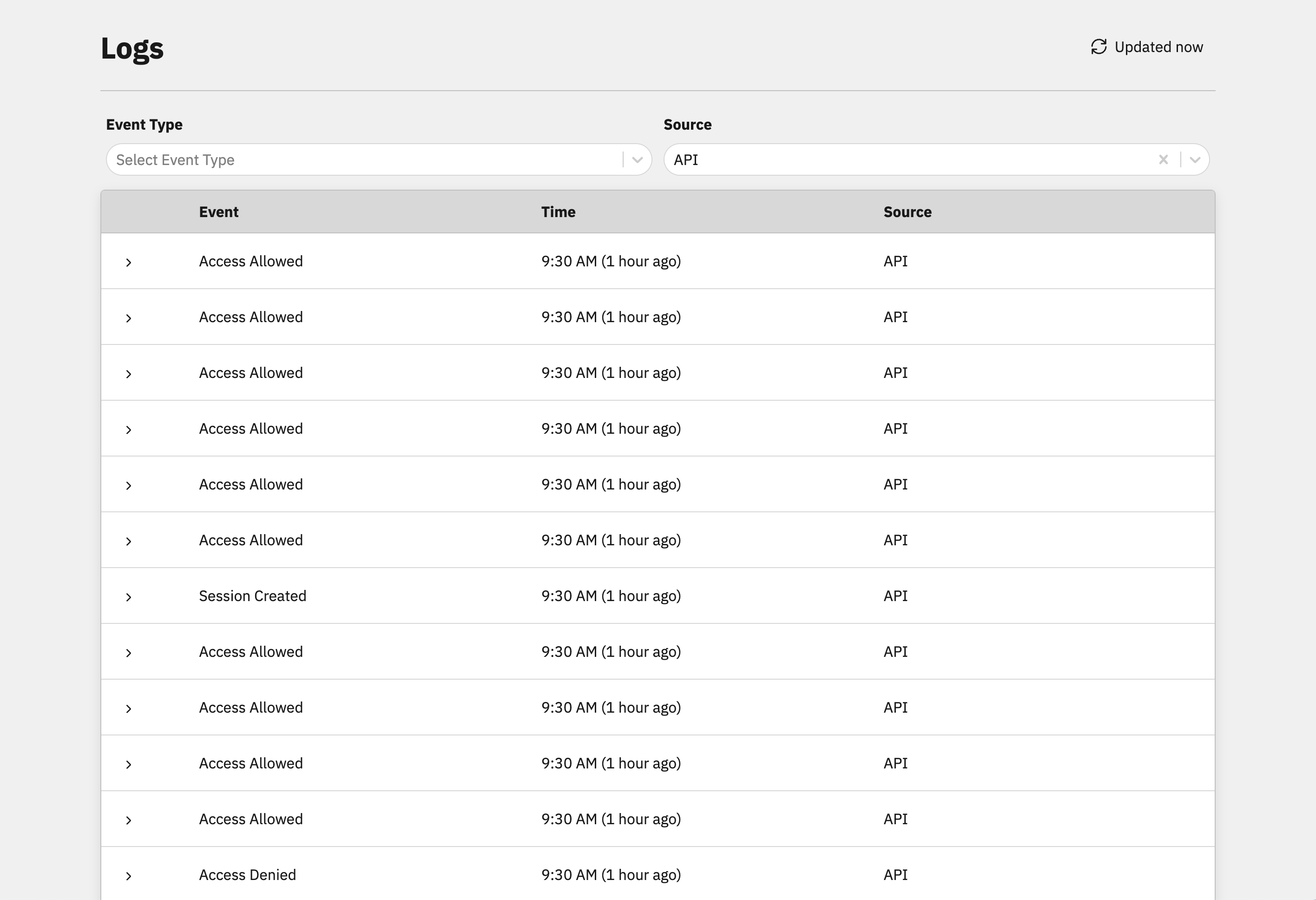
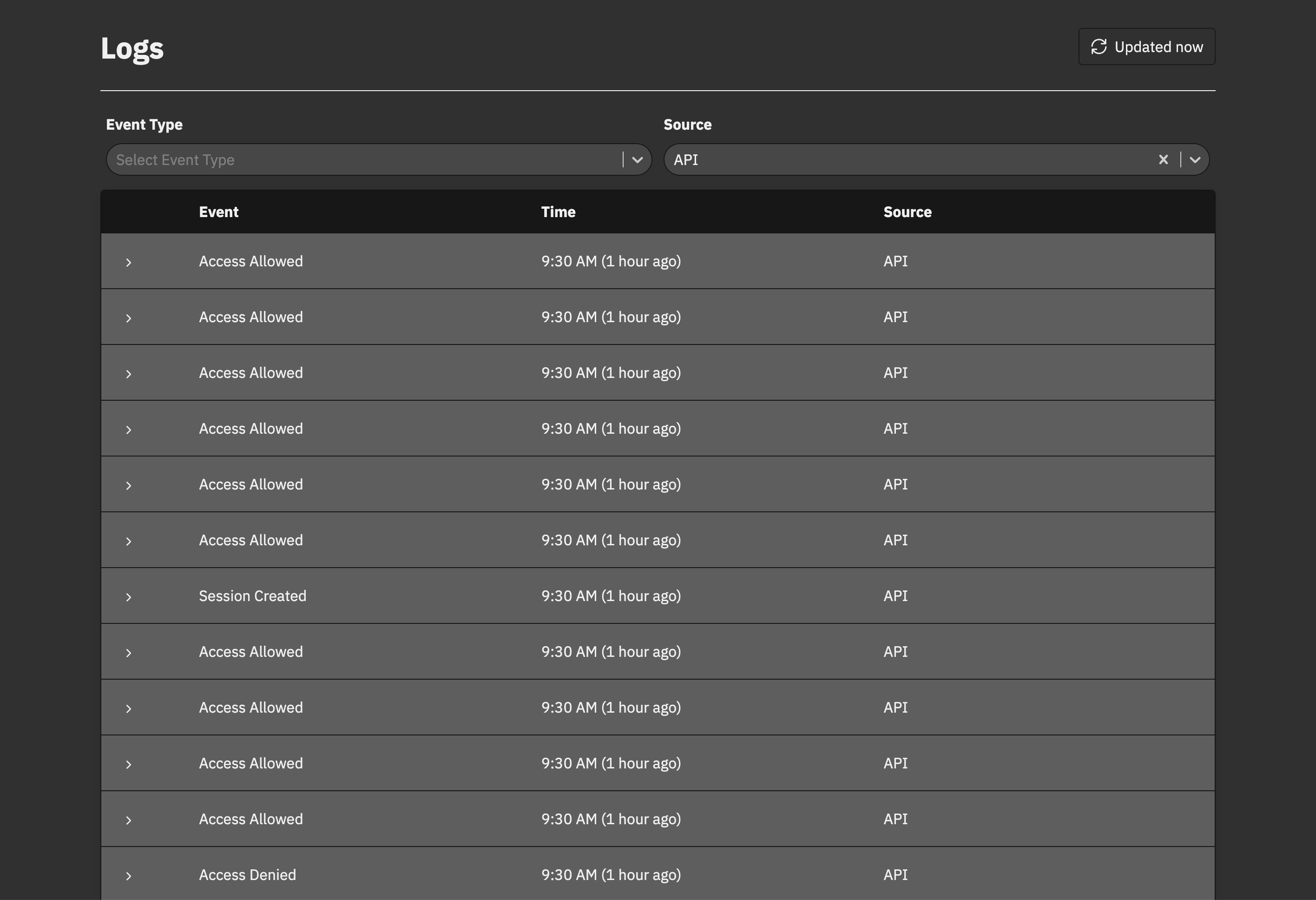
Comprehensive Audit Logs
Audit changes to policies and entitlements and monitor every policy evaluation along with its inputs and its result, making it easy to meet compliance standards like SOC 2, HIPAA, ISO 27001, and PCI.1# Approve txns under the limit.2txn.amount <= user.txnLimit3
4# Authenticate verified users.5user.isVerified == 16
7# Disallow users from the given IPs.8none([9 "192.168.1.1",10 "134.54.15.11"11], user.client_ip)12